Using LXD on your Chromebook
Stéphane Graber
on 26 February 2019
Tags: Chrome OS , chromebook , LXD

Introduction
On supported Chromebook, starting with Chrome OS 69, a new feature called Linux Apps was introduced.
This allows Chrome OS users, on supported to install normal Linux applications from the Debian repository and have them integrate with the underlying Chrome OS desktop.
The feature has evolved quite a bit since its introduction, including recent work on getting sound, USB and even GPU acceleration to those applications.
Getting started
On a supported Chromebook, search for “Terminal” in your application list.

Selecting it will trigger installation of the Linux Apps support package:


Once installed, you get presented with a terminal emulator on a system called penguin:
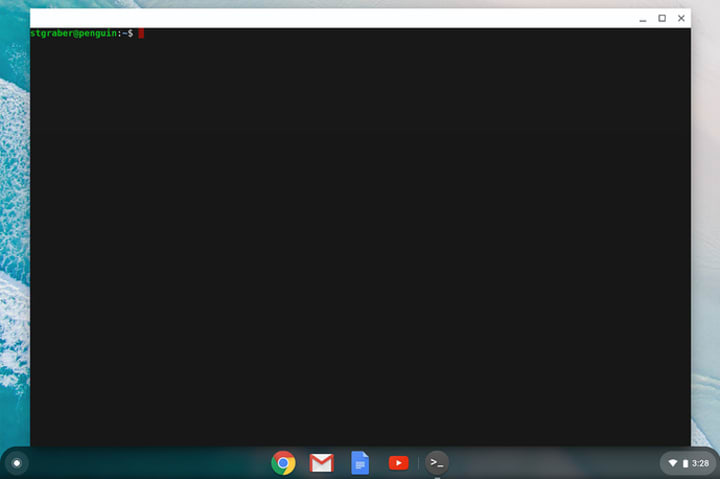
From there, you can install regular Debian packages:
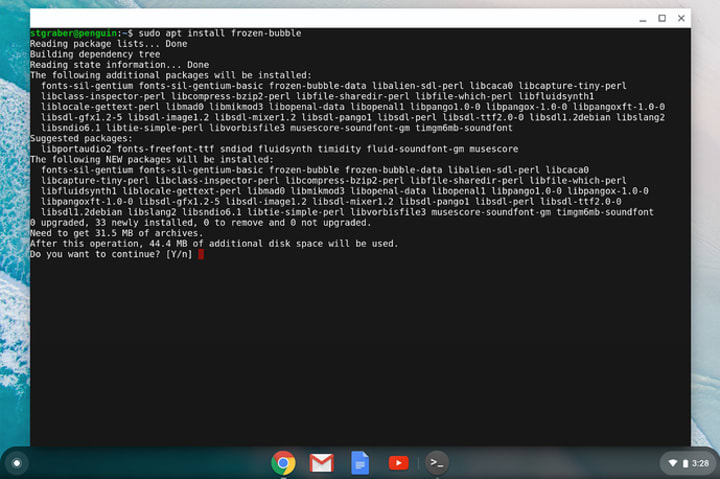
When installing something that comes with a GUI, the appropriate launcher will be added to your Chrome OS launcher. Click on it, and it’ll start the program:
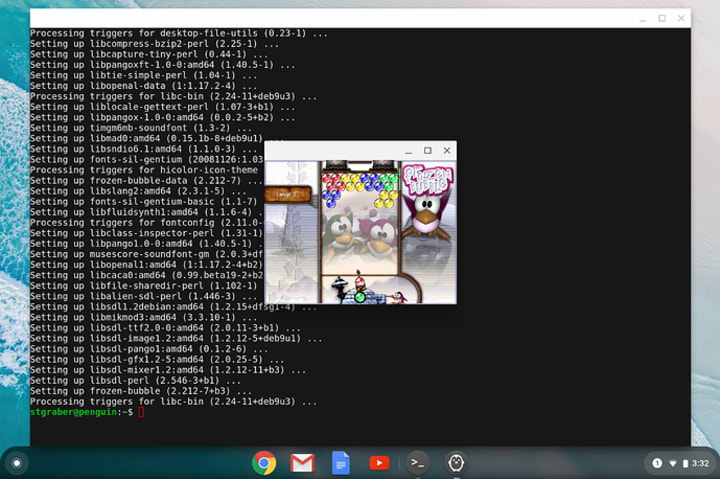
Pretty nice and simple, even comes with integration in the file explorer!
Under the hood
Where it gets interesting is how this was all put together.
Chrome OS is designed to be extremely safe, as much of the system as possible is read-only with the majority of user data stored in the cloud and synced as needed.
So how is it that you can now get root access and install whatever you want on your Chromebook?
Well, containers, LXD containers specifically.
When you install the Linux apps support, a small read-only virtual machine is setup (it’s called termina), LXD runs inside that virtual machine and is provided some amount of persistent storage for the containers.
A default container, called penguin is then created for you from a small Debian based image distributed by Google. That container is passed a number of devices and sockets so it can interact with the Chrome OS desktop.
ChromeOS itself also knows how to interact with the container to pull things like the list of installed desktop applications, access the files stored in the container, …
Using LXD directly
So the default setup is nice and all, but this all means that you actually do have a working LXD daemon on your Chromebook, so can’t you start more containers, run different Linux distributions, … ?
Yes, yes you can.
The first thing you’ll want to do is get into the VM itself rather than inside the container.
To do so, you need to get a crosh terminal by pressing <ctrl>+<alt>+t, this will look like this:
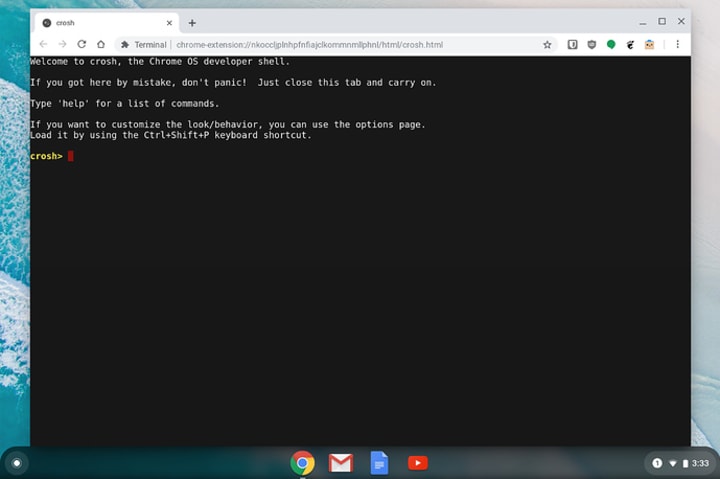
Now run: vmc start termina
This will get you a shell inside the termina virtual machine.
From there, you can directly interact with LXD:

As you can see, there is that penguin container running in there.

And you can launch a few more containers of various Linux distributions and interact with LXD as you normally would on any system.
Getting the LXD client tool inside the penguin container
Having to do that crosh and vmc dance every time you want to interact with LXD may get a bit annoying after a while. Not to mention that termina is seriously locked down so it’s not a particularly great environment to work from.
As LXD can be driven over the network, how about we access it from that penguin container instead?
First thing, you’ll want LXD to listen to the network and setup a trust password, do this from within termina with:
- lxc config set core.https_address :8443
- lxc config set core.trust_password some-password
Then we’ll want to copy a working LXD client that will work on Debian.
If you followed the previous instructions, you’ll have an Ubuntu 18.04 container called c1 which conveniently come with a pre-installed version of the LXD client which we can copy into the penguincontainer.

With that done, you can now get yourself a normal Terminal shell and run:

Here you need to look for the gateway address of the penguin container, this will be the termina VM and so the address of our LXD server. After that, you add it as a remote and make it the default remote so all LXD commands go to it by default.
After that, you can interact with LXD exactly as you would on any other system, including now having a nicely working shell to drive it from
Low level details
For this feature to be supported, you need a Chromebook that’s still actively supported by Chrome OS and have hardware support for virtualization. Both x86_64 and aarch64 machines will work with this feature.
LXD is configured in a way which only allows for unprivileged containers to be run.
This combined with the intermediate virtual machine that’s used on a per-user basis makes the entire environment extremely safe and makes attacking the host largely impossible (you’d need both a container & VM escape).
Currently most Chromebooks use LXD 3.0.0 but an update is actively rolling-out now bringing them to 3.0.2. Storage is using btrfs, allowing for fast container creation, snapshots and copies.
It’s possible to install and run Docker inside the LXD container though not all images will work properly as they may not have been designed with unprivileged containers in mind and so may be surprised when some specific actions are rejected by the kernel.
Other resources
There is a great sub-Reddit for users of Crostini:https://www.reddit.com/r/crostini
LXD documentation: https://lxd.readthedocs.io
List of LXD images: https://images.linuxcontainers.org
The original version of this blog was posted here.
Fast, dense, and secure container and VM management at any scale
LXD brings flexible resource limits, advanced snapshot and networking support, and better security — all making for easier, leaner and more robust containerised solutions and VMs.
Newsletter signup
Related posts
Join Canonical in London at Dell Technologies Forum
Canonical is excited to be partnering with Dell Technologies at the upcoming Dell Technologies Forum – London, taking place on 26th November. This prestigious...
Canonical announces the first MicroCloud LTS release
Canonical announces the first MicroCloud LTS release. MicroCloud 2.1.0 LTS features support for single-node deployments, improved security posture, and more...
Join Canonical in Paris at Dell Technologies Forum
Canonical is thrilled to be joining forces with Dell Technologies at the upcoming Dell Technologies Forum – Paris, taking place on 19 November. This premier...
